The recent global Microsoft outage caused by a faulty update from cybersecurity firm Crowdstrike has had widespread repercussions, affecting millions of Windows computers worldwide. This incident, which has been dubbed a catastrophic failure, highlights the vulnerabilities inherent in relying on third-party software for critical system operations.
Overview of the Microsoft Outage
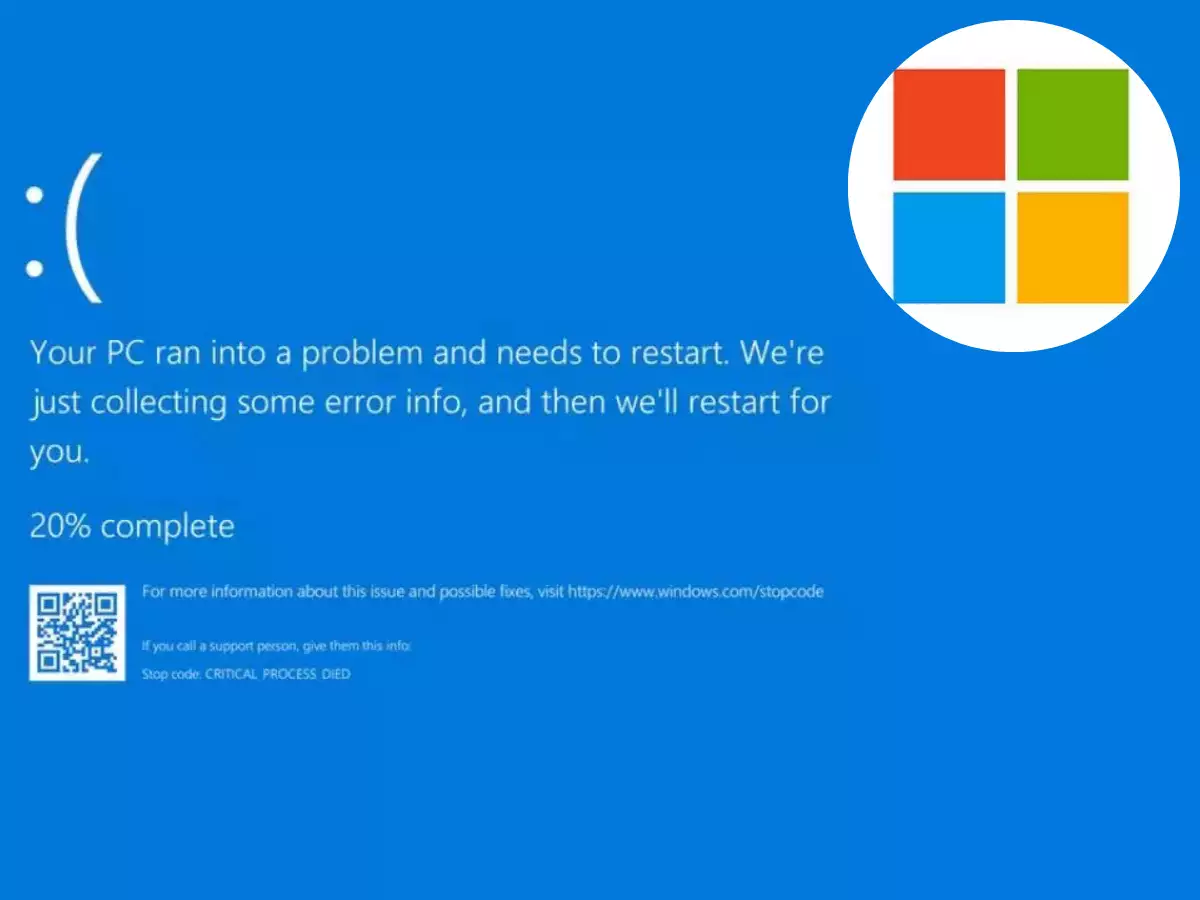
On July 19, 2024, an automated software update from Crowdstrike introduced a serious error that caused a massive number of Windows machines to enter recovery mode, resulting the infamous “blue screen of death.” This disruption was not limited to individual users. It impacted numerous Fortune 500 companies, airports, hospitals, and banks, leading to significant operational challenges. The scale of this outage is unprecedented, with estimates suggesting that billions of Windows computers were affected globally .
Technical Breakdown of the Failure

To understand how such a significant failure occurred, it is essential to examine how Crowdstrike’s Falcon software operates. Falcon integrates deeply with the operating system to provide endpoint protection, often utilizing kernel mode drivers. This integration allows it to monitor system activity and detect anomalies in real-time. However, this also means that if the software encounters a critical failure, it can bring down the entire computer system.
A piece of bad code included in the latest update caused the Microsoft outage. When this code was deployed, it effectively caused the computers that received it to become “bricked,” necessitating IT departments to manually reboot and intervene to rectify the issue. Chaos erupted in workplaces that rely heavily on technology for daily operations, as many employees lost access to their systems.
Impact of Microsoft outage on Various Sectors
The repercussions of the outage affected multiple sectors. For instance, the London Stock Exchange experienced disruptions, affecting trading activities. In India, the need to revert to manual processes for boarding passes forced several airports into a significant setback in an industry that relies heavily on technology for efficiency. Hospitals faced challenges in patient care, as systems that manage patient records and treatment protocols went offline. Banks also reported issues, complicating transactions and customer service operations.
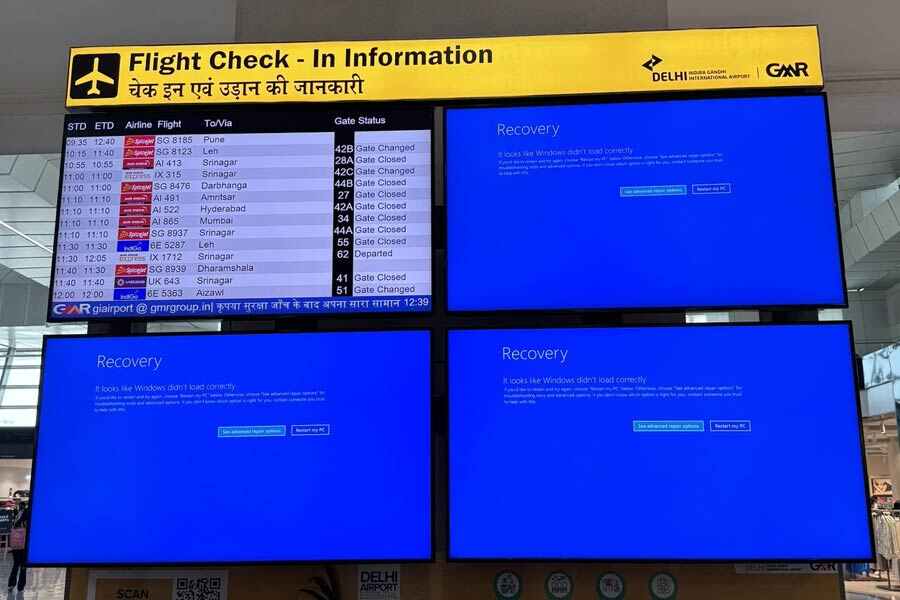
The incident has drawn criticism towards Crowdstrike. In fact many companies that rely on their services are now questioning the reliability of their cybersecurity measures. While Crowdstrike quickly clarified that this was not a security breach or cyber attack, the damage to their reputation and client trust is evident. The company acknowledged the error and is working on solutions, but we cannot overlook the immediate chaos it caused.
The Bigger Picture: Cybersecurity Risks
This incident raises critical questions about the cybersecurity industry’s reliance on third-party software. The fact that a single update could lead to such widespread failure illustrates the risks associated with granting kernel-level access to external vendors. Companies often outsource their cybersecurity needs to firms like Crowdstrike, which can create a single point of failure. This incident serves as a warning. As the very systems designed to protect against cyber threats can themselves become vulnerabilities if not managed properly.
You might also like : Nothing CMF Phone 1: A Promising Newcomer in the Nepali Smartphone Market
Moreover, the incident has sparked discussions about the need for more robust testing and quality assurance processes in software updates. As organizations increasingly depend on technology for essential functions, the consequences of software failures can be dire, affecting not just individual companies but also the broader economy and public services.
Conclusion
The global Microsoft outage caused by Crowdstrike’s faulty update is a stark reminder of the complexities and risks associated with modern cybersecurity practices. As businesses navigate the digital landscape, it is crucial to reconsider how they manage software dependencies. As well as ensure that robust safeguards are in place to prevent similar incidents in the future. The fallout from this event will likely lead to increased scrutiny of cybersecurity protocols. Also a reevaluation of the reliance on third-party services for critical infrastructure.



